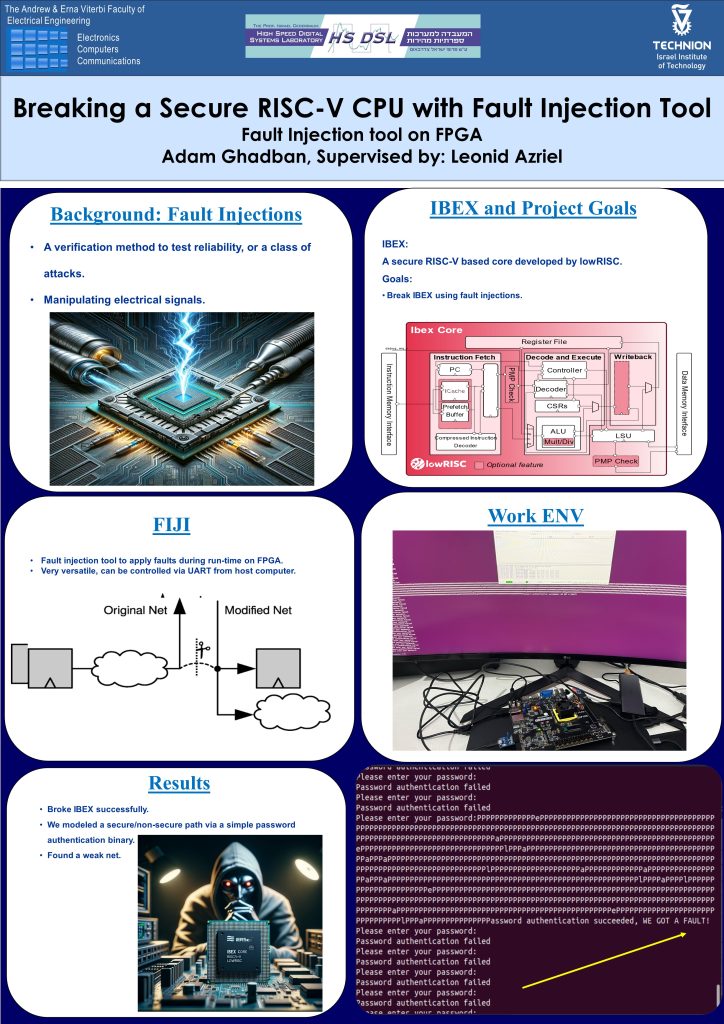
This project verifies IBEX core, a RISC-V based core, on robustness against fault injections, either attacks or natural causes.

In contemporary technology, hardware plays a pivotal role across various domains, from CPUs in personal computing devices to specialized machine learning accelerators in data centers, and even in critical compute and communication applications in aerospace.
These hardware systems are susceptible to faults, which may arise naturally due to phenomena like bit-flips from electromagnetic radiation or transistor aging, or through deliberate fault injections. Given this vulnerability, it is essential for engineers and scientists to assess and ensure the resilience of hardware designs against such faults, particularly to guarantee their long-term functionality in diverse environments.
When evaluating a design’s robustness, the choice between simulation and emulation is influenced by factors like speed, temporal and spatial accuracy, and flexibility. In scenarios where speed is prioritized over accuracy, emulation is often the preferred approach. Following this rationale, our project employed an emulation strategy, leveraging the speed advantages it offers.
This project utilized a pre-existing tool called FIJI, to test the resilience of the IBEX core with activated security features, developed by lowRISC company as an open-source RISC-V based core. FIJI enables the injection of faults into various nets of a synthesized design and facilitates the real-time activation of fault models through UART communication from a host computer to an FPGA.
Our experiments focused on disrupting the IBEX core by injecting faults into flow control nets with pseudo-randomized activation timings. This approach successfully compromised the IBEX core and provided valuable insights into the design’s robustness, offering a clear perspective on its resilience under fault conditions.