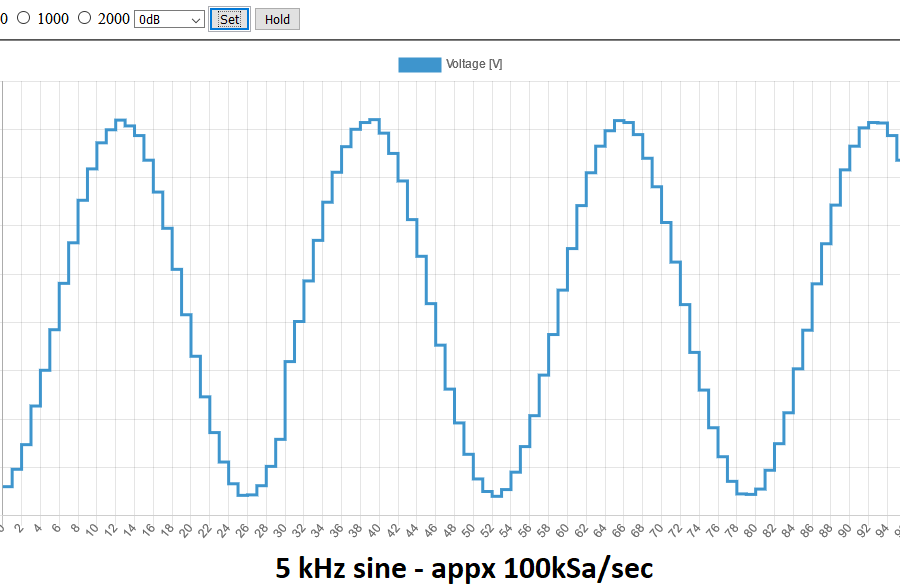
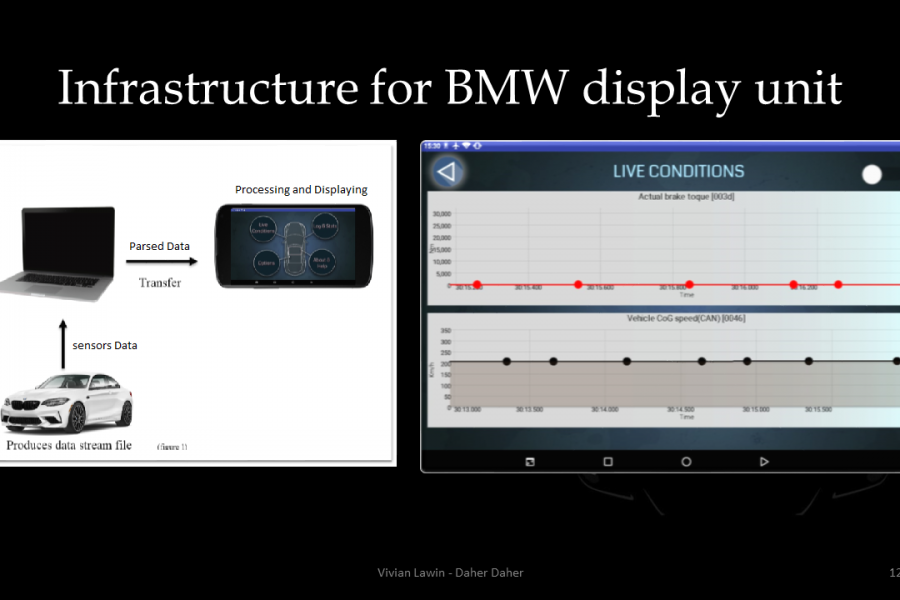
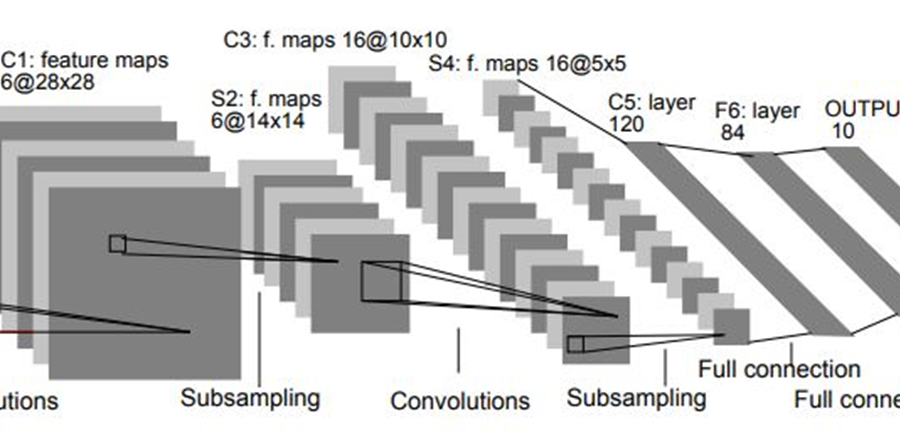
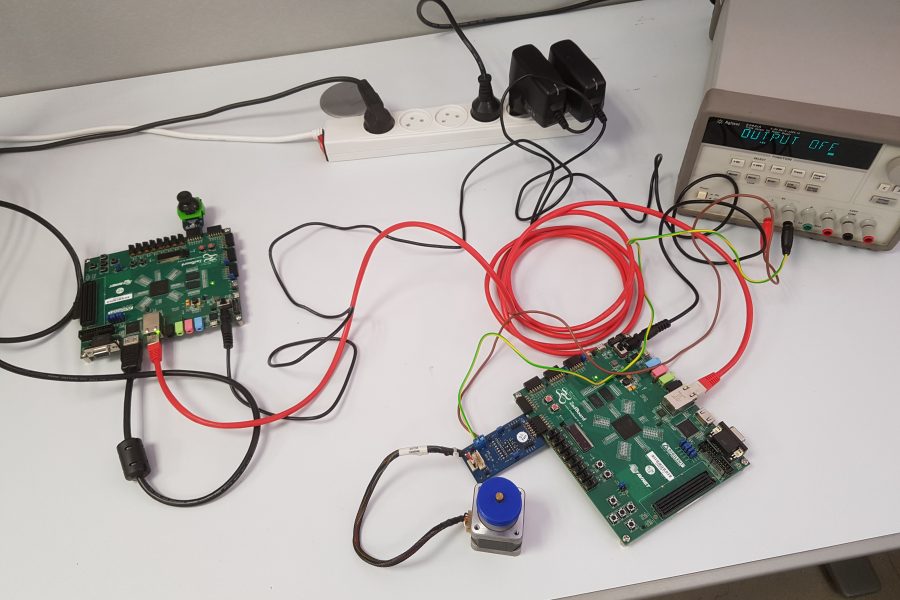
A top (aka dreidel) is a common toy which spins rapidly. The main goal of the project is to design and implement a synchronization system for such a top. i.e., a real time system to indicate the current angle that the top is facing while it is spinning. This solution it to later be used to synchronize different operations.
Categories:
Embedded Systems